What are MFA alerts
MFA alerts monitor for degradation in an M365 environment's MFA posture, by evaluating the state of the users' MFA.

Why should I monitor MFA
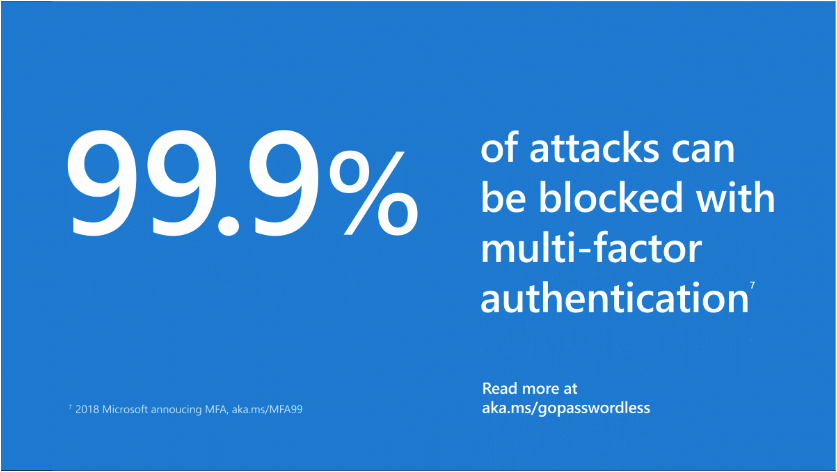
As per Microsoft, 99.9% of cyberattacks can be prevented simply by enabling MFA. Monitoring your customer's MFA posture ensures that they remain compliant and hardened against attacks.
Alert Logic
MFA regression (admin and user):
Hardcoded logic based on the following:
Logic is not evaluated at the time the integration/feature enablement. We don't want to hammer your inbox with notifications for nothing
Daily comparisons evaluated(previous days record at scan time vs new record at scan time)
Alert is sent if a previous days record was compliant (MFA required) and the new record is non-compliant (MFA not required). **Note here that while the risk delta could have regressed by a user no longer requiring MFA, they could still be enrolled, but the lack of requirement means they could also disable MFA, leaving a security risk. This is why we chose to focus on MFA required vs enrollment, as MSP's typically are in control of enforcing the requirements
When a new user is added to the environment without MFA requirement, a notification will not be generated, as that is their baseline state. This avoids unnecessary notifications for things like Service Accounts.
Email Notification Layout
Subject; <user/admin> MFA Alert for <tenant>
Tenant: <tenant>
Discovered on: yyyy-mm-dd
===========
Name: <user1>
Email: <email1>
Previous State: Enabled (yyyy-mm-dd)
Current State: Disabled (yyyy-mm-dd)
Name: <user2>
Email: <email2>
Previous State: Enabled (yyyy-mm-dd)
Current State: Disabled (yyyy-mm-dd)
